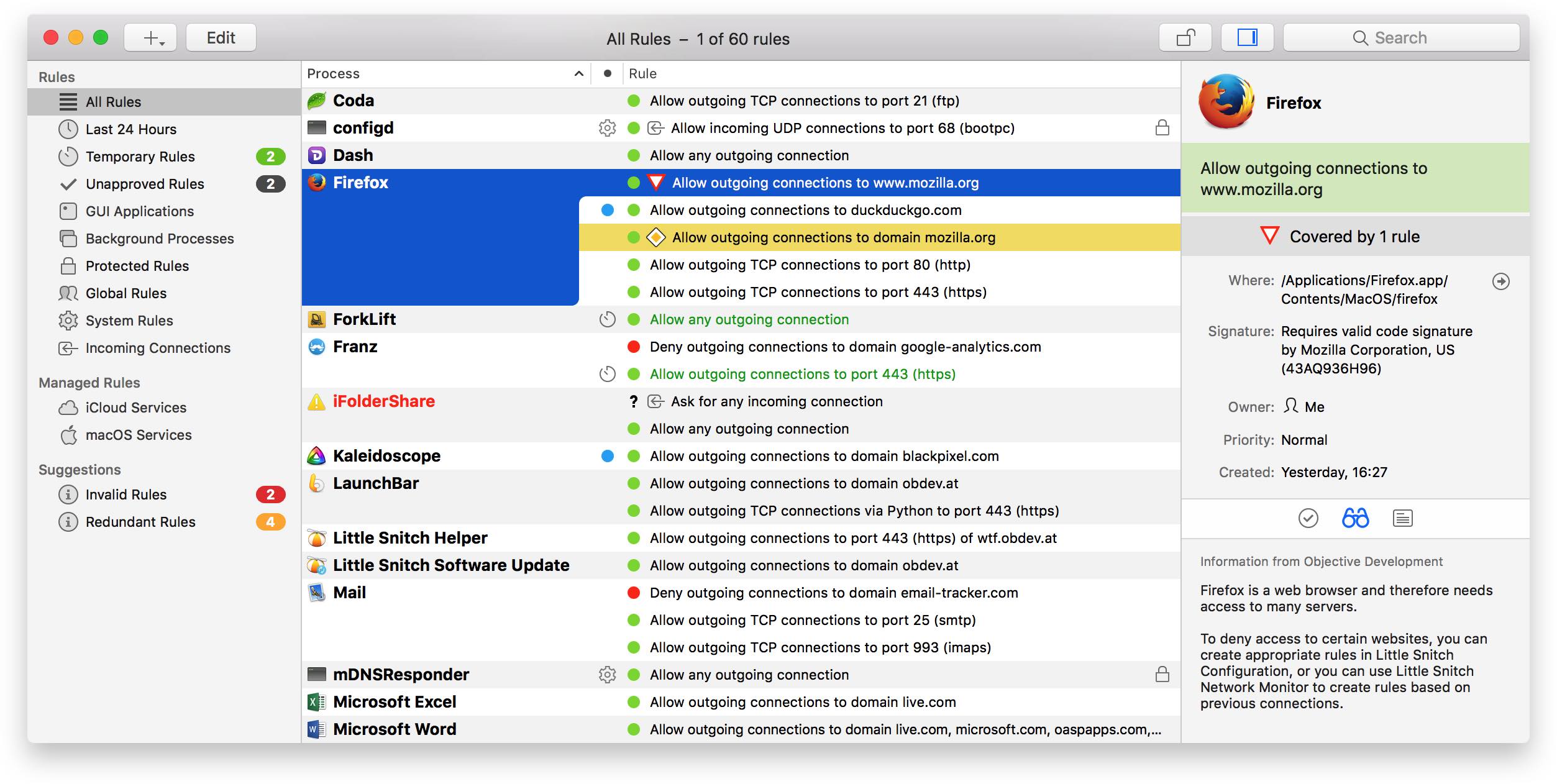
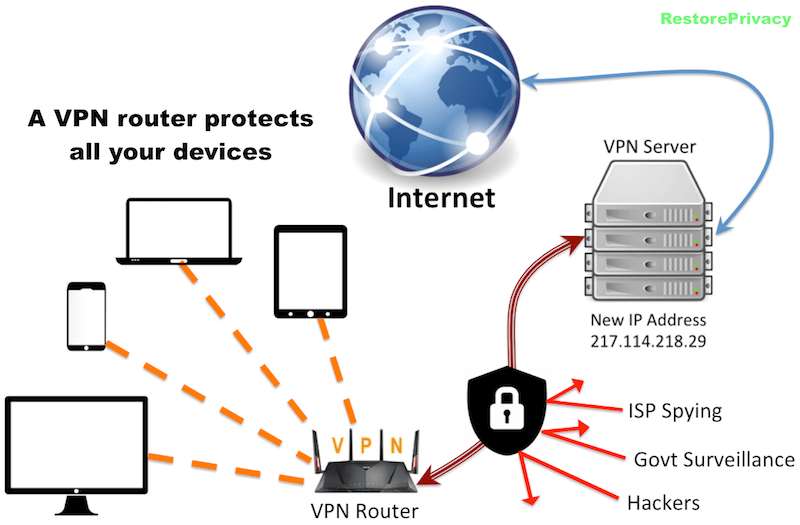
Blocking Tor With Little Snitch
Jan 31, 2018 31 Jan 2018 Block Coinminers with Little Snitch and CoinblockerList on Mac. If you are an OSX Little Snitch user you can use freely available CoinBlockerLists to block large portion of JavaScript based Coinminers like coinhive etc. Did your computer fans suddenly start to go all ballistic on you while browsing the internet? Jul 14, 2019 On investigation Little Snitch appeared to be blocking the connection and reports the reason as; The identity check detected a modification of the program. Therefore all of its connections were denied as a precaution. Nov 22, 2017 Re: Little snitch started blocking all traffic. When something is blocked, Network Monitor flashes the connection line in red. Drill down to a specific connection line by clicking disclosure triangles. Then right-click the line to get a context menu. Little Snitch is not available for Windows but there are plenty of alternatives that runs on Windows with similar functionality. The most popular Windows alternative is GlassWire, which is free.If that doesn't suit you, our users have ranked 25 alternatives to Little Snitch and 13 are available for Windows so hopefully you can find a suitable replacement. Oct 07, 2019 The latest installer for LittleSnitch, 4.4.3, is completely broken. It says you have to allow “Objective Development” as an approved developer in System Preferences. However, when you run the. After hundreds of custom Snort rules that either resulted in an unacceptable number of false positives or stopped working because the TOR client generated new unsigned security certificates that I was able to capture from the packet payload, I determined that the best way to block the TOR traffic and identify it was to block the traffic from.
Starting with macOS 10.15.4 the above “Legacy System Extension” message will be shown when Little Snitch is installed.
→ Please read this blog post to learn more about why this message is shown.
Will there be an update of Little Snitch that’s compatible with macOS 10.16?
Yes. We are going to release Little Snitch 5 later this year, which will be compatible with macOS 10.16. → Learn more…
Will I get the update for free?
Yes. All licenses sold now include a free upgrade to Little Snitch 5. In addition, customers who purchased Little Snitch 4 within a one-year period prior to the final release of Little Snitch 5 will also get a free upgrade. → Learn more…
Will Little Snitch 4 run on macOS 10.16?
Little Snitch 4 will not be loaded on macOS 10.16 by default, but there will still be an option to allow the loading. → Learn more…
This guide came about spending hours upon hours of “sniffing” (capturing) network traffic in search of any common factors in identifying TOR traffic in our network. After hundreds of custom Snort rules that either resulted in an unacceptable number of false positives or stopped working because the TOR client generated new unsigned security certificates that I was able to capture from the packet payload, I determined that the best way to block the TOR traffic and identify it was to block the traffic from reaching the TOR exit nodes.
12 Steps total
Step 1: BACKGROUND
First for some background on our situation and the usage of TOR:
I am employed by a K-12 educational school district located in Texas and our Internet access (including transit charges) are subsidized via the E-Rate program.
With the “sugar” comes a bit of “vinegar”, our Internet usage must comply with CIPA (Child Internet Protection Act) and several other regulatory guidelines or we risk losing the federal subsidized funding for our Internet access and transit. We have in place AUP’s (Acceptable Use Policies) that outline what is acceptable, what is not and the consequences that may occur for violation of these policies.
In order to be in compliance with CIPA and other regulations we have Internet monitoring, traffic shaping and content filters in place.
This How-To is not about what is right and what is wrong about content filtering and censorship.
I am a network administrator and have been tasked with making sure that our network is in compliance with our school district’s AUP’s, CIPA, etc.
In a nutshell, from my packet captures with Wireshark , tcpdump , and other programs, initially connects via TCP port 9001, then tries TCP port 9090, then starts “port hopping” (jumping from TCP port to port) to make an initial connection with a TOR exit node. Once the initial connection is made, the traffic primarily uses TCP/443 (HTTPS/SSL/TLS) with the traffic payload being encrypted. The TOR client creates its own self-signed SSL certificate using a random common name (domain name) that changes after approximately every 30 minutes.
After going around and around with this scenario without success, I decided to try and block access to the TOR exit nodes from our network. There are several ways to attack this problem, either create and update router ACL’s (access control list) or our main firewall ACL’s.
For the sake of simplicity for our particular network environment, I chose to work with our main Internet router ACL’s. We are a Cisco shop but the same principles can be applied to Linux iptables, other router and firewall manufacturers.
Step 2: My Network Administrator toolbox used on my workstation (Windows 7 64bit Enterprise)
You Linux users might/will be familiar with several of these programs that have been ported over to Windows. If you are more comfortable using this technique to block TOR traffic using a Linux box then go for it.
1. ActiveState Tcl Community Version – free download http://www.activestate.com/activetcl/downloads
a. If you are running a 64bit OS, download and install the 32bit version, the next step will only work with the 32bit version of ActiveState Tcl
b. After installation, run “teapot.ext install Expect” (case sensitive) to install the expect package. Expect will be used to automate the ACL update process discussed later in this whitepaper. Linux expect users take note: the ActiveState Expect package does not follow the exact same structure as the Linux distribution of Expect.
2. Notepad++ - http://notepad-plus-plus.org/ - used for batch file creation and tcl and txt file examination
3. Wget for Windows - http://gnuwin32.sourceforge.net/packages/wget.htm
4. Microsoft Visual Studio 2010 – this is what I use on my workstation. The process that I use could be ported over to VBScript or other scripting/programming languages. Just use the one you are familiar with.
5. TCLTelnet 2.0.1 - This will make your expect automation a lot simpler
Step 3: Time to get into the meat of the subject!
After searching the Internet, I found this web site: https://www.dan.me.uk, ok another web site. This website has page, https://www.dan.me.uk/torlist/, with just the TOR exit node IP addresses, 1 IP address per line. This page is updated every 30 minutes, but you can only access the page 1 time
Step 4: Getting Started
1. Install or verify installation of the pre-requisite programs listed above.
2. Note the installation path for the wget program, you may need to use the short filename path to execute this program (I had problems using the full path names on my 64bit system with wget, I had to use the short filename path C:Progra~2GnuWin32binwget.exe to execute the program).
Step 5: Create a Working Directory
Create a working directory on your computer to hold your files you will be working with (i.e. C:TOR-ACL, or C:Die-TOR
Step 6: Create a new batch file
Create a new batch file (.bat or .cmd) in your working directory (i.e. TOR-ACL-Creator.cmd)
Since the URL to the TOR exit list is https, you will need to use the --no-check-certificate so wget will not check for SSL certificates.
So the first few lines of your batch file will look similar to:
@echo off
C:
CD TOR-ACL (change to your working directory)
C:Progra~2GnuWin32binwget --no-check-certificate https://www.dan.me.uk/torlist/
This will download the TOR exit node list to a file called, get ready, index.html. This file is plain text and contains no html code with 1 TOR exit node IP address per line, similar to the following:
101.1.131.133
101.142.83.155
101.98.134.31
103.4.16.118
106.187.34.237
106.187.36.183
106.187.36.240
… so on and so on
Step 7: Using Visual Basic or VBScript
This is where the scripting or where I used Visual Basic to do my magic with.
Loop through the index.html file until the end of file is reached
As you are looping with a Do While not EOF statement
Read in each IP address into a variable (I used TorIP as my variable name)
You have 2 choices here, do you want to manually update your ACL or do you trust your programming to update your ACL for you. I cheated a little. Our router’s ACL that I use for the TOR traffic is a Cisco extended ACL #150.
For testing, I used an extended ACL that I numbered 151 but did not assign to an interface until I was happy with the results of the whole process, download of the TOR list, creation of the Tcl file, running the Tcl file through expect to remove the old ACL and update the new ACL our router. Then I just changed the source code back to ip access-list extended 150 from the ip access-list extended 151, added in the code to update the interface with the access list 150.
I check the ACL (access-list) every few days to be sure it is right, and then I write the config to the startup config. This way if the download is bad or the ACL update goes bad, at worst case scenario I can just reboot the router to reload the last known good config that was saved to the startup nvram.
If you do not want to automate the process, write your script or program to write the ACL or iptables to a text file that you can paste into your terminal emulator, then apply the ACL or restart the iptables.
Step 8: Write the contents of our ACL or iptables file that is static
Write the contents of our ACL or iptables file that is static information first before writing the TOR IP list.
file.WriteLine('config t')
file.WriteLine('interface gig 0/1')
file.WriteLine('no ip access-group 150 in')
file.WriteLine('no ip access-group 150 out')
file.WriteLine('exit')
file.WriteLine('no ip access-list ext 150')
file.WriteLine('ip access-list ext 150')
file.WriteLine('remark -- Updated by _
TOR-AccessList Creator')
file.WriteLine('remark ---- Current Revision: ' _
+ Format(Now).ToString + ' -----')
file.WriteLine('deny tcp any any eq 9001')
file.WriteLine('deny tcp any any eq 9090')
With the TOR IP address in the variable (i.e TorIP in my case), write the output line as you would need it from the i. statement above such as:
File.writeline(“deny ip host “ + TorIP + “ any”)
Step 9: Writing static information at the bottom of the file
After the end of file is reached, add the static information you need at the bottom of your ACL or iptables file
file.WriteLine('permit ip any any')
file.WriteLine('exit')
file.WriteLine('interface gig 0/1')
file.WriteLine('ip access-group 150 in')
file.WriteLine('ip access-group 150 out')
file.WriteLine('exit')
file.WriteLine('exit')
file.WriteLine(')
Step 10: Sample of the TCL-Expect Code:
For clarity, variables dimensioned (Dim’ed)
Dim DblQuote = Chr(34)
Dim crlf = Chr(10) + Chr(13)
file1.WriteLine('#!/tcl/bin/tclsh')
file1.WriteLine('# ')
file1.WriteLine('exec tclsh ' + DblQuote + '$0 ${1+ ' + DblQuote + '$@' + DblQuote + '}')
file1.WriteLine('package require Expect')
file1.WriteLine(crlf)
file1.WriteLine('log_user 1')
file1.WriteLine(crlf)
file1.WriteLine('exp_spawn tclsh.exe telnet_test.tcl 216.xx.xxx.xx 23')
file1.WriteLine(crlf)
file1.WriteLine('expect ' + DblQuote + 'Username' + DblQuote + ' {')
file1.WriteLine('exp_send ' + DblQuote + 'usernamer' + DblQuote)
file1.WriteLine('}')
file1.WriteLine(crlf)
file1.WriteLine('expect ' + DblQuote + 'Password:' + DblQuote + ' {')
file1.WriteLine('exp_send ' + DblQuote _ + 'myrouterpasswordr' + DblQuote)
file1.WriteLine('}')
file1.WriteLine(crlf)
file1.WriteLine(RtrPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'config tr' + DblQuote)
file1.WriteLine(crlf)
file1.WriteLine(ConfigPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'interface gig 0/1r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(InterfacePrompt)
file1.WriteLine('exp_send ' + DblQuote + 'no ip access-group 150 inr' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(InterfacePrompt)
file1.WriteLine('exp_send ' + DblQuote + 'no ip access-group 150 outr' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(InterfacePrompt)
file1.WriteLine('exp_send ' + DblQuote + 'exitr' + DblQuote)
file1.WriteLine(crlf)
file1.WriteLine(ConfigPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'no ip access-list ext 150r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(ConfigPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'ip access-list ext 150r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(ACLPrompt)
'file1.WriteLine('exp_send ' + DblQuote + 'remark -- Updated by TOR-AccessList Creatorr' + DblQuote)
file1.WriteLine(crlf)
file1.WriteLine('exp_send ' + DblQuote + 'remark ---- Current Revision: ' + CurrentDate + ' ' + CurrentTime + ' -----r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(ACLPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'remark ---------------------------------------r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(ACLPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'remark --- TOR Ports ---r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(ACLPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'deny tcp any any
eq 9001r' + DblQuote)
'file1.WriteLine(crlf)
file1.WriteLine(ACLPrompt)
'file1.WriteLine(crlf)
file1.WriteLine(ACLPrompt)
file1.WriteLine(ACLPrompt)
file1.WriteLine('exp_send ' + DblQuote + 'remark -- TOR Exit Nodes --r' + DblQuote)
'file1.WriteLine(crlf)
As you can see the TCL/Expect script/program output is in a different format, when the program runs and completes you will end up with a TCL file looking like the following:
#!/tcl/bin/tclsh
#
exec tclsh '$0 ${1+ '$@'}
package require Expect
log_user 1
exp_spawn tclsh.exe telnet_test.tcl 216.xx.xxx.xx 23
expect 'Username' {
exp_send 'myusernamer'
}
expect 'Password:' {
exp_send 'myrouterpasswordr'
}
expect 'GISD-ATT-RTR#'
exp_send 'config tr'
expect 'GISD-ATT-RTR(config)#'
exp_send 'interface gig 0/1r'
expect 'GISD-ATT-RTR(config-if)#'
exp_send 'no ip access-group 150 inr'
expect 'GISD-ATT-RTR(config-if)#'
exp_send 'no ip access-group 150 outr'
expect 'GISD-ATT-RTR(config-if)#'
exp_send 'exitr'
expect 'GISD-ATT-RTR(config)#'
exp_send 'no ip access-list ext 150r'
expect 'GISD-ATT-RTR(config)#'
exp_send 'ip access-list ext 150r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'remark ---- Current Revision: Thursday, May 17, 2012 12:30:02 PM -----r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'remark ---------------------------------------r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'remark --- TOR Ports ---r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny tcp any any eq 1390r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny udp any any eq 1390r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny tcp any any eq 9001r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny udp any any eq 9001r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny tcp any any eq 9090r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny udp any any eq 9090r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'remark -- TOR Exit Nodes --r'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny ip host 101.1.131.133 anyr'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny ip host 101.142.83.155 anyr'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny ip host 101.98.134.31 anyr'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny ip host 101.98.162.41 anyr'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny ip host 103.4.16.118 anyr'
expect 'GISD-ATT-RTR(config-ext-nacl)#'
exp_send 'deny ip host 106.187.34.237 anyr'
snipped /norton-for-mac-and-little-snitch.html.
Step 11: Complete your batch (.bat/.cmd) file
@echo off
C:
CD TOR-ACL (change to your working directory)
C:Progra~2GnuWin32binwget --no-check-certificate https://www.dan.me.uk/torlist/
C:TOR-ACLTOR-AccessList-Creator.exe (Whatever you named your program)
Or
C:windowssystem32cscript TOR-AccessList.vbs (Your VBScript script name here)
del c:Tclbinlog.txt
c:
cd tclbinc:tclbintclsh.exe c:tclbinTor-Access-List.tcl > c:Tclbinlog.txt
As you can see in the last line, I piped the output to a text file.
Little Snitch Crack
Step 12: Create your scheduled tasks
I created 2 scheduled tasks with Windows Scheduler.
The 1st task runs the batch file above once every hour.
This pulls down the new TOR exit node information, manipulates the data and outputs the files I need to update our router ACL, then it updates our router ACL using tclsh and expect for Windows.
The second task, emails me the log file and is set to run 3 minutes after the 1st task starts.
This way I get a log file record of the access-list updates that were applied.
This is my first SpiceWorks HowTo, so be gentle on me.
I hope that this helps someone down the road and that someone can gain some useful information from my hours of frustration of going through packet traces.
Please comment on this if you find it helpful or just another waste of your time!
If you see something I missed documenting, please let me know.
Little Snitch Mac
References
- ActiveState Tcl Community Edition
- CIPA - FCC website
- CIPA - Wikipedia
- E-Rate
- Notepad++
- Snort
- tcltelnet 2.0.1
- tcpdump
- TOR Exit Node list - IP addresses, 1 per line
- TOR Project
- wget for Windows
- Wireshark
9 Comments
- DatilEngineerIT Jul 20, 2012 at 06:03am
Very clever! didnt think this was possible
- PimientoNyr Nov 25, 2012 at 01:59pm
This isn't a clever way to block Tor traffic. You aren't blocking Tor traffic, only public Tor nodes.
How to bypass this blocking? Just ask for private bridges here:
https://bridges.torproject.org/Also, the website you link isn't listing Tor exit nodes only, public bridges are listed too and it's a different thing. For example, someone who wants to block abuse from the Tor network would only want to filter exit nodes and not bridges.
A bulk list of Tor exit nodes can be obtained directly from the Tor Project website:
https://check.torproject.org/cgi-bin/TorBulkExitList.py - SerranoIron Man Mar 5, 2013 at 09:42pm
@Nyr. Could not have said it better. This is not really blocking Tor. :) The Tor does not like to be blocked. :)
- ChipotleMJReno Apr 13, 2013 at 07:52pm
This is a good guide to stop kids/staff circumventing filters. Agreed on using bridge IPs.
As a sidenote, although people misuse Tor, it also does a lot of good, so I only recommend blocking it is abused.
Thnkx for sharing.
- Anaheimjohn galbraith Dec 18, 2013 at 09:53pm
@MJReno I see your point there but, if you read his original backstory before getting into the nitty gritty of how he was blocking traffic, he was stating that he was trying to be in compliance with CIPA. Allowing any access to TOR would be a very thin grey line given the sheer amount of negative influences, services, and the overabundance of child pornography found within the TOR network. I would say that this guy is doing the right thing here.
- Pimientogregory.thomson.906 May 23, 2014 at 08:26am
Just getting started at understanding TOR. So, it's the exit node that does the final connect to the destination web site, and then returns the response to the TOR browser, so blocking those exit node IP's from getting back through the firewall into your network effectively keeps the page from rendering in the TOR browser? The traffic doesn't go back through the same sequence of nodes it went through to send the request? I work in K-12 too, not looking to censor, just block bad stuff for the K-12 age range.
- Pimientomichaelmoore4 Jan 18, 2015 at 06:10am
I am experiencing the problem where my roommate is blocking Tor. I have tried changing my IP address, useing The bridges from TOR & spoofing my MAC address none have been a success any suggestions????
- Pimientoseanobriainbcommcisa Jun 12, 2015 at 08:46am
Talk to your roommate. (non tech solution to non tech problem)
- Pimientosmookie Jan 31, 2019 at 09:03am
The problem is that this won't work, because of these things called Tor plugable transports and these other things called Tor bridge nodes. (both of which come packaged with Tor.) Tor Plugable transports (such as meek) disguise the Tor protocol by using ports commonly used by other services (such as port 80 or port 443) to communicate with a Tor bridge node. What's more, is that you will not find the addresses of Tor bridges published anywhere on some list- as Tor keeps these a well guarded secret. Effectively this means that the user can establish a Tor circuit by effectively disguising their Tor traffic to look like regular HTTP or HTTPS traffic using the plugable transport , and then connect to a 'secret' guard node known as a bridge node. (packet sniffing and DPI won't work with meek servers either- as meek was designed to circumvent packet sniffing and Deep Packet Inspection.) This cocnnection technique is highly effective because entire countries (such as China as a primary example) cannot effectively manage to block amazon-meek without blocking normal web traffic to basically every HTTPS service hosted on an amazon cloud server. This post only demonstrates that the OP has an extremely poor working knowledge and understanding of how Tor Works. I do have to give brownie points for the attempt though.